Abstract
What are some useful entry technologies on the Web2.0 journey to Web3.0?
In the evolution from Web2.0 to Web3.0, data, asset account and application interoperability are two key issues. The former involves consensus transmission between different ecosystems, including on-chain and off-chain consensus transmission; The latter is a practical problem in the process of application deployment. Although the world of Web3.0 is as vast as the sea of stars, the evolution of Web2.0 to Web3.0 requires continuous exploration in practical technology and credit transmission mechanism.
At present, zero-knowledge proof and EVM are two very practical technologies, which have become two important entrances of the evolution from Web2.0 to Web3.0. Zero-knowledge proof provides a convenient and practical verification method, so that data/accounts outside Web3.0 (off-chain) can easily obtain on-chain verification, gain the trust of the Web3.0 ecosystem, and provide the possibility for data/asset exchange. At the same time, the current so-called Web3.0 ecosystem is mainly built on Ethereum, and docking with ethereum ecological flow becomes an important entrance to the Web3.0 world. As a result, EVM becomes an extremely useful infrastructure and technology. The Web2.0 ecosystem can also try to interoperate applications with ethereum through EVM compatibility.
Zero-knowledge proofs can share computing functions, with only security and validation on the chain. A combination of zero-knowledge proof and consensus on the blockchain can reduce the cost of a network where a single device can run a computation, where cryptography is used to verify its reliability on the chain rather than participating in the computation twice, and where costly blockchain networks are used, it is much cheaper to verify the correctness of the computation than to double calculate it. Thus, blockchain is only responsible for the consensus and security of the network, while some of the computational work can be handed over to zero-knowledge proof and done outside the blockchain network. Overall, this approach not only improves scalability, but also retains the security and consensus of blockchain networks. This point is highlighted in our “where do Web3.0 applications run? This is detailed in the report. Representative projects of zero-knowledge proof applications include zkSync, Mina, etc.
Due to ethereum’s strong ecosystem, EVM is the quickest route for other public chains to deploy their original Ethereum ecosystem applications (such as DeFi application protocol). Ethereum relies on EVM for asset accounts, contract execution, and the ERC family of tokens (including THE ERC20 standard token and THE ERC721 standard NFT). A platform that deploys EVM interconnects with Ethereum in token standards, contract procedures, and so on. This means that the original Ethereum ecosystem application protocol can be seamlessly translated to the new public chain deployment, and EVM also makes experiencing dApps on other public chains virtually non-sensory for its users, much like operating on Ethereum. Suffice it to say, EVM deployment is standard on most public chains.
Not only does EVM provide a “lazy” and useful entry point to the non-ethereum public chain for actual application deployment, but we can’t help but wonder if the Web2.0 ecosystem can seamlessly integrate with ethereum in terms of data state, asset accounts, and contract programs through EVM deployment. Can you imagine a scenario in which a stock exchange deploys EVM to enable asset transfer and interoperability with ethereum or even other Web3.0 ecosystems? Blockchain synthetic asset platforms like Synthetix, Mirror and UMA are equivalent to creating the shadow and mapping of Web2.0 assets in the Web3.0 world. Can EVM make Web2.0 assets directly and directly enter the Web3.0 world? For example, access to the Web3.0 world directly via email or mobile phone number? In any case, EVM is a very pragmatic infrastructure application.
Risk tip: blockchain business model landing less than expected; Regulatory policy uncertainty.

At present, domestic attention to Web3.0 is increasing day by day. In addition to recognizing its characteristics of openness, sharing and privacy, how to migrate to Web3.0 based on the existing application scenarios and development capabilities has become an important issue. Web3.0 is not empty talk, and there is a lot of underlying logic and technology that needs to be sorted out.
In the evolution from Web2.0 to Web3.0, data, asset and application interoperability are two key issues. The former involves consensus transmission between different ecosystems, which also includes on-chain and off-chain consensus transmission; The latter is a practical problem in the process of application deployment. Although the world of Web3.0 is as vast as the sea of stars, the evolution of Web2.0 to Web3.0 requires continuous exploration in practical technology and credit transmission mechanism.
At present, zero-knowledge proof and EVM are two very practical technologies, which have become two important entrances of the evolution from Web2.0 to Web3.0. Zero-knowledge proof provides a convenient and practical verification method, so that data/accounts outside Web3.0 (off-chain) can easily obtain on-chain verification, gain the trust of the Web3.0 ecosystem, and provide the possibility for data/asset exchange. The current so-called Web3.0 ecosystem is basically built on Ethereum, and the ecological traffic connected to Ethereum becomes an important entry point into the Web3.0 world. As a result, EVM becomes an extremely useful infrastructure and technology. The Web2.0 ecosystem can also try to interoperate applications with ethereum through EVM compatibility.
Gateway to Web3.0
There is no doubt that on the road to Web3.0, the Web2.0 value ecosystem and data will coexist for a long time and will continue to merge. So, what is the gateway from Web2.0 to Web3.0? There are two key questions: first, how does credit transfer between two ecologies in the presence of obvious barriers? For example, does Web2.0 ecosystem data get consensus across the Web3.0 chain? How do Web2.0 assets connect with Web3.0 accounts? Secondly, if the programs between the two ecosystems need to interoperate, in the actual application deployment, different program languages will bring great difficulties in deployment, which is a very practical problem in the landing process.
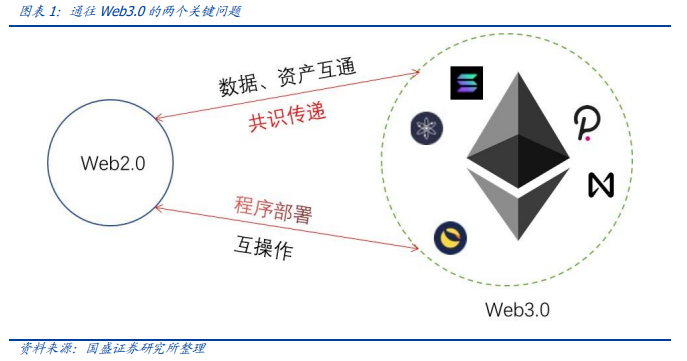
In the current so-called Web3.0 ecosystem, the ethereum ecosystem is the absolute workhorse. Docking of Web3.0 ecology, often can start from docking ethereum ecology. A large number of non-Ethereum public chains share ethereum’s ecological traffic by deploying EVM. Not only does EVM provide a “lazy” and useful entry point to the non-ethereum public chain for actual application deployment, but we can’t help but wonder if Web2.0 can use EVM to seamlessly integrate with ethereum in terms of data state, asset accounts, and contract programs. Can you imagine a scenario in which a stock exchange deploys EVM to enable asset transfer and interoperability with ethereum or even other Web3.0 ecosystems? Blockchain synthetic asset platforms like Synthetix, Mirror and UMA are equivalent to creating the shadow and mapping of Web2.0 assets in the Web3.0 world. Can EVM make Web2.0 assets directly and directly enter the Web3.0 world?
Zero-knowledge proof and EVM are two very practical technologies in the Web3.0 ecosystem, and are also expected to set up a “portal” between Web2.0 and Web3.0.
Two practical technologies of Web3.0: zero knowledge proof and EVM
This chapter introduces zero knowledge proofs and EVM respectively. Typical examples of zero knowledge proofs include zkSync, MINA and other projects. EVM is almost standard for non-Ethereum public chains, and recently EVMOS and Filecoin’s FVM are emerging. As a virtual machine based on storage public chain, FVM has other different characteristics.
3.1. Zero-knowledge proof
Zero-knowledge proof (also known as minimum disclosure proof) is undoubtedly one of the most popular terms in the blockchain industry recently. Zero-knowledge proof was first proposed by MIT professors and cryptography experts in the 1980s. Zero knowledge proof refers to the fact that the prover can prove the authenticity of a statement to the verifier without disclosing any other information. Nowadays, zero-knowledge proof is mainly applied to blockchain. Its excellent mathematical properties can be used in many different scenarios. Zero-knowledge proof technology is still in its very early stages.
Let’s say A has A box with A combination lock. He wants to convince B that A knows the password to the box without telling B the real password. So what is he going to do?
A asks B to write A secret that only B knows all over the world. B writes A note “My dog’s name is Bob” and puts it in the box. A opens the box with the correct password and gets this information and informs B. In this interaction, B didn’t get any information (the password of the box) that he didn’t know before, but A still succeeded in convincing B that A knew the password.
It was initially thought that proof was an interaction between people in face-to-face communication. As counterintuitive as it sounds, randomness can be used to prove something. An ideal proof should have no randomness or uncertainty. Zero-knowledge proof is a complete subversion of the traditional concept of proof. In traditional proof, randomness is completely contrary to what the prover is trying to achieve. The prover will strive to make the entire flow of information public. But once the idea is reversed and there is no longer an attempt to expose the flow of information, the negative side of randomness becomes a positive, and randomness can be exploited to hide information that is intended to be hidden.
3.1.1 Zero-knowledge proof principle
Zero-knowledge proof, an encryption method developed by MIT researchers in the 1980s, is one of the cryptographic algorithms widely used in trusted computing. Zero-knowledge proof or zero-knowledge protocol is a probabilistic verification method consisting of two parts: prover that claims a proposition to be true and verifier that the proposition is indeed true.
As the name implies, zero-knowledge proof means that one can fully prove that he is the legal owner of certain rights and interests without leaking out relevant information, that is, the “knowledge” given to the outside world is “zero”. Zero-knowledge proof has three properties:
(1) Completeness. If both the prover and the verifier are honest and follow every step of the proof process and perform correct calculations, then the proof must be successful and the verifier must be able to accept the prover;
(2) Rationality. No one can impersonate the certifying party and make the certification successful;
(3) Zero knowledge. After the proof is performed, the verifier only gets the information “the prover has the knowledge”, but not any information about the knowledge itself.
The formal definition of zero knowledge must use some computational model, the most common being the Turing machine computational model, and in the case of Turing-complete Ethereum, this combination with zero knowledge proof has spawned L2 applications such as zkSync.
3.1.2 Significance of zero-knowledge proof
From the perspective of application, zero-knowledge proof has two very important directions:
1) Privacy: zero-knowledge proof can satisfy the privacy of messages. For example, in blockchain transactions, if you need to prove that you own some unused asset, but do not want to expose the details of the asset, zero-knowledge proof technology can solve common blockchain networks due to the disclosure of information due to transparency, such as address and asset amount.
Privacy computing is an important application field of zero knowledge proof. Privacy is a problem caused by information leakage. If you want to protect privacy, you must use cryptography solutions to encrypt the data on the chain so that there is no correlation between the different transactions on the chain. Zero-knowledge proofs can verify calculations without exposing any information about the input and calculation itself, ensuring on-chain data privacy.
One of the most important things in Web3.0 is that users themselves have real ownership of identity and data. However, all information on the current blockchain is public, and users’ information can be easily accessed through some means (which of course is also a characteristic of the blockchain network consensus). Although blockchain users do not have a broad and strong sense of privacy at present, with the development of the future, this need will certainly be more urgent and long-term. So to realize the vision of Web3.0, users must have the right to have their own on-chain privacy. So it’s safe to say that privacy is not necessarily optional, but it’s definitely optional.
2) Extensibility: if the common blockchain platform takes a long time to verify a new block, it can be directly changed to one person (node) to verify and generate a proof. Other participants in the network can master the method to verify the proof quickly, without requiring each participant to spend a lot of time to directly verify.
This involves the cost of consensus. From an economic point of view, blockchain networks such as Ethereum and Bitcoin have high transaction costs because consensus has to be expensive, and cheap consensus is to some extent unreliable. The cost comes mainly from the double calculation of several devices under the consensus of blockchain. For example, in a POW consensus mechanism (such as Bitcoin, Ethereum, etc.) network, the efficiency of 1000 machines doing repetitive computation is no more than that of a single computer, but the cost can be simply thought of as 1000 times that of a single device doing the same computation. This is the cost that all mainstream consensus protocols, whether POW or POS, have to pay to ensure decentralized consensus. The binding of an impossible triangle.
A combination of zero-knowledge proof and consensus on the blockchain can reduce the cost of a network where a single device can run a computation, where cryptography is used to verify its reliability on the chain rather than participating in the computation twice, and where costly blockchain networks are used, it is much cheaper to verify the correctness of the computation than to double calculate it.
Thus, blockchain is still responsible for the consensus and security of the network, while some of the computational work can be handed over to zero-knowledge proofs outside the blockchain network. Overall, this approach not only improves scalability, but also retains the security and consensus of blockchain networks. This point is highlighted in our “where do Web3.0 applications run? This is detailed in the report.
3.1.3 Zero-knowledge proof technology and application
Zk-snarks (compact non-interactive zero-knowledge proofs), ZK-Starks (compact all-transparent zero-knowledge proofs) and bulletproof proofs are the three common techniques for zero-knowledge proofs. Two of these are used by blockchain projects: ZK-SNARks and ZK-Starks.
Both technologies are combined with ZK-Rollup, which is built on top of the L1 main chain. Ethereum, for example, is what we call a “unitary” blockchain. Because consensus, execution, and data availability all happen on the same blockchain. This is why the unitary Ethereum blockchain cannot scale, which is often referred to as the impossible triangle problem. To scale, Ethereum must evolve into a “modular” blockchain. That means using blockchain only for what it does best: consensus. And “outsource” the rest of the work execution and data availability down the chain.
Zk-rollup presents multiple transactions as a single transaction to the main chain (such as Ethereum), which is quickly verified by the main chain with a zero-knowledge proof that is stored on the main chain. Therefore, you can inherit the security of the main chain while porting execution and data availability to ZK-rollup. The main chain does not have to process all transactions individually, so the size of each transaction is compressed, and the cost of validation is spread across all transactions to save Gas and improve TPS. ZkSync and Starkware are the best of the zK-rollup. The two projects have similarly similar architectures: Rollup smart contracts are deployed into the Ethereum blockchain to store ZK proofs of L2 state transitions. The essence of ZKRollup is to compress and store the user status on the chain in a Merkle root (meaning that the rollup contains account balance, contract code, etc.), and transfer the update of the user status to the chain. Meanwhile, the correctness of the user status change process under the chain is guaranteed by zK-SNARks proof. It is relatively high cost to directly process user status update in Layer1, but it is much lower cost to only use the smart contract on the main chain (Layer1) to verify whether a zero-knowledge Proof is correct. This is also the most critical role of zero-knowledge proof.
Zk-starks stands for project StarkWare:
StarkWare invented cryptography based on STARKs proof. It also addresses DA (data availability) issues through the Volition system. (DA is so important that users can see exactly how their transactions are happening in the blockchain browser.) Volition allows users to choose between rollup (on-chain data availability, which is more expensive) and Validium (off-chain data availability, which is cheaper). In the Validium scenario, off-chain DA is guaranteed by a centralized “data availability committee” composed of reputable cryptographic entities. It’s not decentralized but it’s cheaper. Users are still free to choose, which is a compromise.
The advantage is that T stands for Transparent, which means no trust Settings are required. It also generates proofs faster. (Some studies suggest that STARKs proofs can be generated up to 10 times faster than SNARKs.) The disadvantage is that the technology is not as mature as SNARKs, and if it is Turing complete, it is difficult to be compatible with EVM. StarkWare created a specific programming language to run the autonomic programs it supported. StarWare is currently creating a code shifter to seamlessly convert Solidity into its particular language Cairo for EVM compatibility. It has the characteristics of fast proof and verification, but large proof volume.
Representative project of ZK-SNARKS technology zkSync:
Ethereum founder Vitalik believes that “in the medium to long term, ZKRollup will eventually win out in all scenarios as zK-Snark technology improves.” It can be seen that ZK-SNARK has obvious advantages, but it is technically difficult. The project that represents this is zkSync.
ZkSync is a low-cost, trust-free expansion protocol based on the ZKRollup architecture for scalable low-cost payments on Ethereum. The security of user assets is ensured through zero knowledge proof and data availability. All funds are held by smart contracts on the main chain, while computing and storage takes place outside the main chain. To improve efficiency, rather than validate each transaction individually, the transaction is “aggregated” into a single item (a summary block, or Rollup) and then validated, approving all transactions at the same time.
The main architecture of zkSync is divided into on-chain and off-chain, namely L1 and L2. The core of L1 is zkSync smart contract, which is mainly responsible for deposit, withdrawal and transaction verification, namely the maintenance of the final state of the account on the main chain of Ethereum. L2 is divided into L1 interaction (Watcher, Sender), L2 state maintenance (Mempool, BlockProposer, StateKeeper, BlockCommiter), and zero-knowledge proof system.
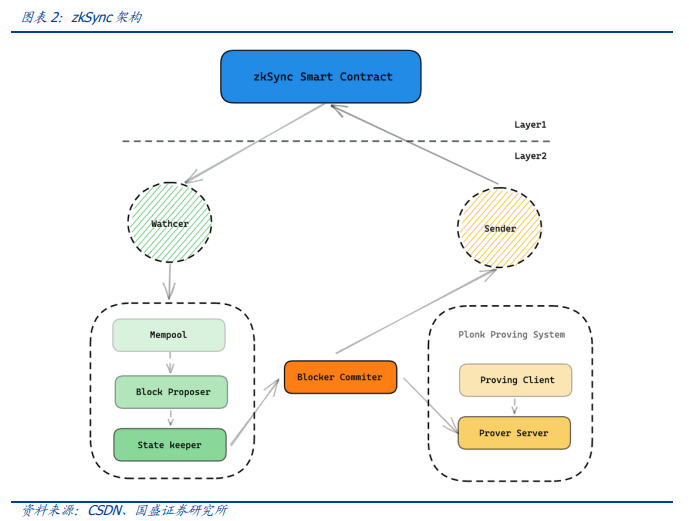
The user signs the transaction and submits it to the verifier;
It is submitted to the verifier;
The verifier aggregates thousands of transactions in a block and submits to the smart contracts on the main network the cryptography promise (root hash) of the new state and the cryptography proof that the new state is indeed the result of the new state to apply some correct transactions to the old state;
In addition to proof, status (refers to a small amount of data for each transaction) is published on the main chain network ata cheap price calldata, which allows anyone to reconstruct the status at any time;
Proofs and status are verified by smart contracts to verify the validity of all transactions contained in the block and the availability of block data.
ZkSync in the transfer process, StateKeeper notifies the BlockCommiter to collect the required information to generate the zero-knowledge proof. After PlonkProvingSystem is called to generate the zero-knowledge proof, the Sender sends the transaction data such as deposit and transfer. And submit the corresponding zero-knowledge proof to L1’s zkSync smart contract verification; After waiting for L1 to confirm the transaction, Watcher will notify L2 to update the transaction status to final confirmation. Thus, L2, which is separated from the main chain, achieves consensus transmission with the main chain through zero-knowledge proof.
ZkSync has the advantage of achieving EVM compatibility in a more natural way than the ZK-Starks solution. Because smart contracts can be converted one by one by the zkSync compiler, there is no need for a mediation language or a specialized translator. The disadvantage is the slow generation of proofs. In short, zkSync has the characteristics of slow proof, fast verification and small proof volume. As a result, zkSync is the industry’s most promising L2 solution, and its ecosystem is booming with the release of version 2.0.
No matter L2 or L1, on-chain, Web2.0 or Web3.0, zero-knowledge proof can be used to transfer credit. Therefore, zero-knowledge proof, as an effective technology to achieve consensus transmission among different ecosystems, becomes the entrance technology from Web2.0 to Web3.0.
3.2. EVM: The secret of Ethereum’s eco-traffic Express
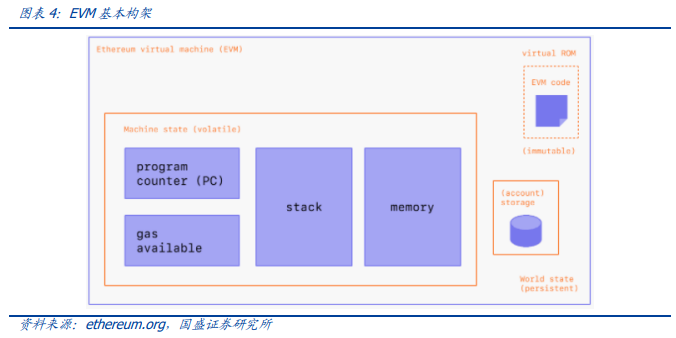
EVM’s full name is EthereumVirtualMachine, the Virtual machine of Ethereum. A virtual machine is a complete computer system running in an isolated environment that can simulate the functions of a complete hardware system through software. EVM is a huge virtual machine that allows code to be deployed and executed. Users simply install the necessary client software to access EVM and use it to execute programs on Ethereum. Because Ethereum is an “Internet computer” consisting of a large number of decentralized nodes, EVM allows users to perform software operations in a decentralized environment. EVM is Turing-complete (in short, it can be used to solve any computable problem) because it can be used to perform computations of all complexity, commonly known as smart contract execution programs. And bitcoin is Turing incomplete, limiting its functional development.
We can think of EVM as a platform or environment for ethereum to execute contract applications, providing users with an application environment platform to deploy applications. EVM exists as a single entity, maintained by thousands of interconnected computers running Ethereum clients. The Ethereum protocol itself exists for the sole purpose of keeping the EVM, a special state machine, running continuously, uninterrupted, and immutably. EVM is the environment in which Ethereum accounts and smart contracts live.
Unlike Bitcoin’s UTXO, which maintains account balances, Ethereum not only maintains account balance status, but also supports more powerful smart contract capabilities. Ethereum is actually not just a distributed ledger, but a distributed state machine.
EVM becomes the most practical and fast entrance for ethereum traffic spillover. We can’t help thinking whether EVM can be introduced into the Web2.0 world. For example, financial platforms such as stock exchanges can deploy EVM, get through the connection with Ethereum, and connect traditional financial assets in the market with DeFi financial assets. So as to promote the integration of traditional financial markets with DeFi markets and stimulate a greater variety of financial services? Currently, users are used to the identity of the Web2.0 social platform. Can they directly log in to the Web3.0 application by deploying EVM? For example, access to the Web3.0 world directly via email or mobile phone number? In any case, EVM is a very pragmatic infrastructure application.
3.2.1EVMOS: EVM compatibility chain of Cosmos Ecology
What Evmos does is integrate the EVM compatibility chain (not just Ethereum) into the Cosmos ecosystem. This means that EVM blockchains such as Fantom, Avalanche and others can integrate assets into the CosmosIBC ecosystem via Evmos. That is, evM-based decentralized applications, tokens, and NFT can all be connected to the Cosmos ecosystem, enabling a true multi-chain ecosystem where users and developers can easily move assets and operate across multiple chains. Evmos originated with Ethermint in 2016 and was originally intended to help scale up Ethereum and EVM applications through the Tendermint Consensus protocol.
Thus, EVMOS will have a unique and indispensable place in the Cosmos ecology. EVMOS is developed using the same CosmosSDK and Tendermint consensus engines as Terra(LUNA),CosmosHub(ATOM), and these technologies have been running steadily for 2-3 years. The biggest difference between Evmos and Cosmos in the existing ecosystem is the introduction of EVM compatibility in the application layer, enabling maximum agility and efficiency in deploying smart contracts developed using the Solidity language, which means that the thousands of existing projects on Ethereum can be seamlessly portable. Evmos also has a special ERC20 module designed to be able to convert cosmic-standard-based tokens into ERC20, making it compatible with Ethereum ecotokens. As a result, Evmos and Ethereum are almost seamless and interoperable. Allow the vast assets on Ethereum to flow into the Cosmos ecosystem and interact with the best native assets in it such as ATOM, LUNA, OSMO. Assets on Ethereum can be extended into the Cosmos ecosystem as a bridge.
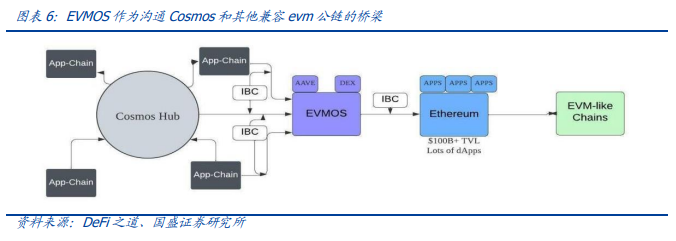
The Cosmos ecosystem lacks a way to borrow against some of the best assets, such as ATOM, but the arrival of EVMOS could be a game changer. Therefore, in the short to medium term, EVMOS is likely to see rapid growth in the total number of users and active transactions (similar to the AvalancheC chain) to meet the diverse needs of other asset holders in the Cosmos ecosystem. This is also the spillover effect of ethereum ecological traffic.
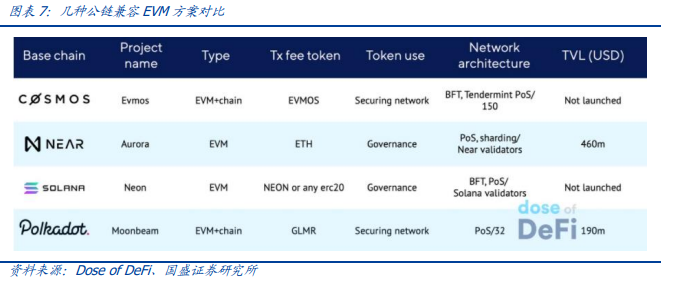
This raises the question of why would-be Ethereum killers are rushing to embrace EVM. Low cost chains (such as Polygon,BSC,Fantom) that run Ethereum virtual machines have achieved success in a relatively short period of time and a relatively prosperous ecosystem. Other more distinctive public chains with different architectures have to think about what EVM means for their respective development and embrace it more quickly. Examples include Moonbeam on Boca, Aurora by Near and EVMOS in Cosmos mentioned above.
When these evM-incompatible chains first hit the market, they often claim to have better, more unique designs and architectures, as well as support for some major programming languages or high-speed features. As these public chains support EVM, it seems that they are less concerned with their own technological advantages and more concerned with ethereum’s vast ecosystem. By embracing EVM, these chains seem to be back to their roots, not screaming to be “Ethereum killers,” but building a lower-cost alternative to Ethereum to capture market share, with a “no fight, join in” feel.
The advantages of EVM compatibility are illustrated in the example of EVMOS such as being an entry point for the influx of assets; A safer EVM bridge; Link their underlying native assets to a broad EVM ecosystem, etc. But there are also disadvantages such as the tool to the etheric fang ecological more prosperity, and the user experience of highly homogenized also brought vicious competition, if a program can be run through all the EVM entry and basic block chain, so want to take the user from their original “greenhouse” attract requires some concrete preferential or the unique advantages, For example, price competition, user subsidies, gameplay innovation, etc.
3.2.2FVM: Storage + computing exploration
Filecoin is a distributed data storage marketplace that distributes content-addressed data sets among storage space providers around the world, increasing the redundancy and resilience of data that is essential to storage infrastructure for innovative application scenarios such as NFT. Filecoin is moving ahead with the gradual introduction of virtual machines (FVMS), integrating basic resources such as storage and computing, which will bring new power to the Filecoin ecosystem.
FVM is a multilingual execution environment based on WASM. WASM, which stands for WebAssembly, is a binary instruction format that runs on a stack-based virtual machine and supports many modern programming languages such as Rust, C++, and JavaScript. WASM was originally designed as a virtual machine for browsers, where different programming languages can be compiled into binary files that run at near-native speed on the CPU. WASM’s host independence, sandbox security, and simplicity make it a better fit for the blockchain space, making it an ideal runtime environment for smart contracts.
The main purpose of FVM is to support the execution of native Filecoinactors (Filecoin’s other name for smart contracts) compiled into WASM format by other programming languages, as well as the execution of external smart contract environments (such as EVM). FVM’s EVM compatibility is out of the box by emulating the underlying bytecode, and allows developers to develop directly with familiar tools like Remix, Truffle, and OpenZeppelin. The vast majority of smart contracts are ported to FVM without any changes.
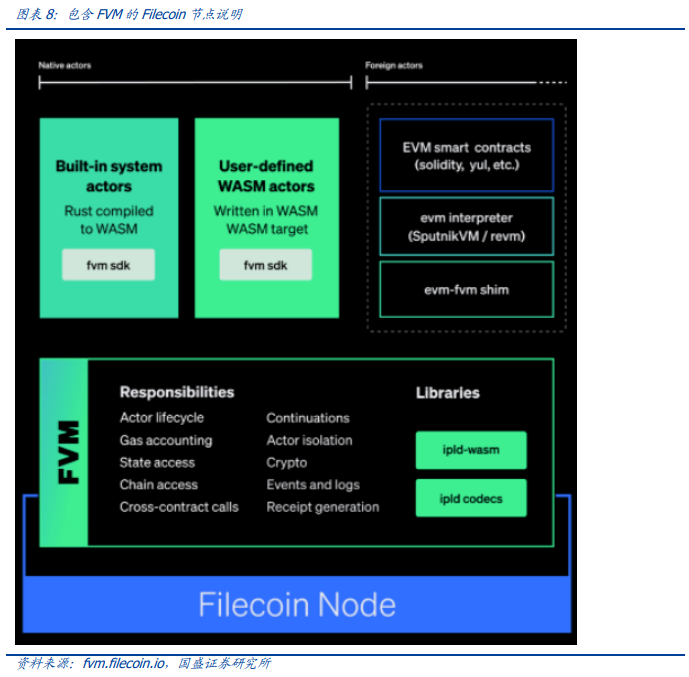
As there is still some time to go online, currently available information is not rich. According to the official disclosed documents and information, the consensus of FliecoinLayer0 itself is still a mixed consensus mechanism of replication proof + space-time proof, while FVM is more likely to introduce a new independent mechanism to guarantee the rewards of computing resource providers. The introduction of FVM has transformed Filecoin from a Web3.0 decentralized storage infrastructure into a public chain with a natural advantage in off-chain data availability. FVM will first provide a better solution for some activities within the Filecoin ecosystem, such as:
1) Decentralized computing of data: computing directly in the space where the data is stored in Filecoin without moving it;
2) Intelligent elastic storage market: dynamic pricing of storage costs based on time, demand, replication level, etc.
3) Storage derivatives (insurance, mortgage, loan) : users can “pre-order” storage space at a specific price, and the data producer will predict their cost over a specific period of time. Instead, by letting storage providers bid on future storage space, they can identify demand in advance, effectively managing inventory, hardware, operations, and finances. Or insurance agreements, for example, can help storage providers raise money from investors for the vast amount of collateral they need to provide services, or distribute risk more broadly. Investors can also collect daily fees to generate cash flow from income.
We believe that the introduction of FVM and its active EVM compatibility will bring a lot of changes to Filecoin itself. Thanks to FVM support, many dapps, including NFT applications and DeFi applications, will change. For example, NFT applications will not need to run IPFS nodes on their own. NFT data may be directly linked to transactions, readily verifiable and reliable, and can be referenced by smart contracts to unify data, calculations, and transactions. If FVM needs to break out of the pack, simply competing with other chains for TPS performance doesn’t seem to be the way to go, but differentiating Filecoin as a storage infrastructure with decentralized storage, storage proof, and verification might unlock more possibilities.